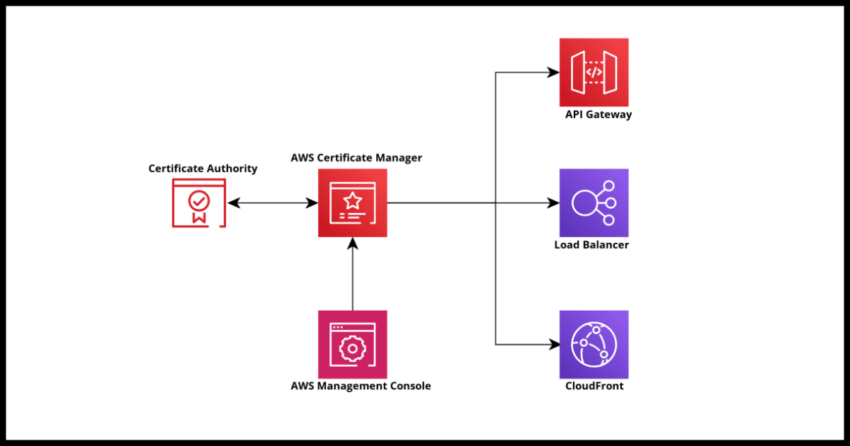
It is a given that we need to associate a valid SSL certificate with any domain that you would actually like to host anything on and this process is typically automatically provided for you as service when you host your site with providers, including Amazon’s Amplify Hosting which automatically creates one for a CloudFront hosted site (like this blog).
But there are certain times where we may need to create SSL certificates directly for use with specialized applications and/or specific Amazon services – such as fronting it against API Gateway endpoints or AppSync custom domains or Elastic Load Balancers. In all these situations, you might need to request a certificate to use if you don’t have one available for your domain. AWS Certificate Manager is a great and cost effective service that can satisfy most needs and also reduces a lot of overhead in maintenance associated with it if your other parts of the infrastructure are already on Amazon Web Services.
This guide walks you through the process of requesting a brand new public SSL certificate for a domain you own screen by screen.
Prerequisite: Having a domain and permissions to create CNAME records for it
To successfully get an SSL certificate issued, you need to pass the DNS validation step – basically proving you either own the domain name – or if you are doing this for a company or client, you need to be able to add CNAME records for the domain to prove ownership or at least management on behalf of. This guide does not cover the more manual email validation process.
In that same note, this guide assumes you have an AWS account where you are able to follow the steps outlined. If you don’t and are just considering AWS Certificate Manager – it is quick and easy to get a free tier account for testing things out and you can always delete the certificate later if you don’t need it.
Initial Certificate Request
Navigate to the AWS Certificate Manager console and you should see the “Request certificate” button quite prominently displayed.
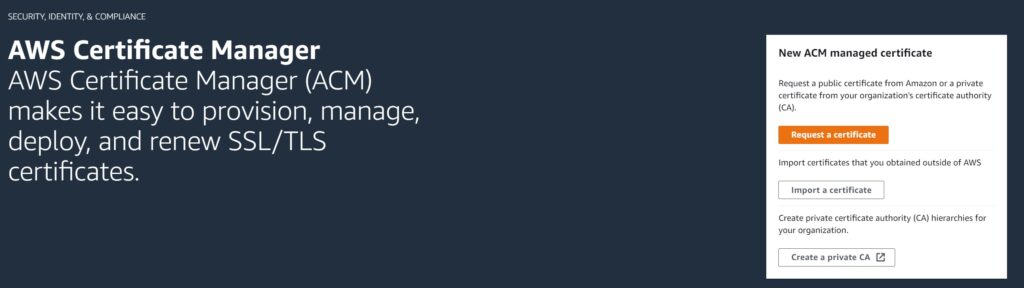
In the next modal, select public certificate. AWS Certificate Manager or ACM can also issue private certs for your organization and the process is quite similar to this guide, but not specifically covering that or its use cases in the screens here.
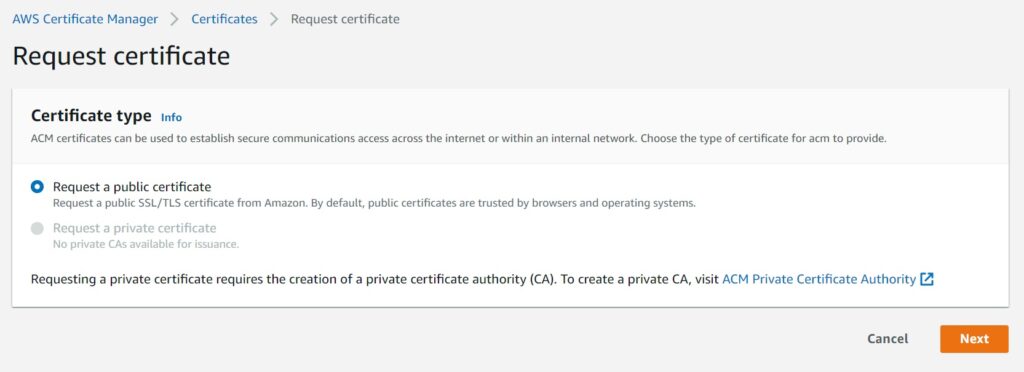
In the next screen – enter the domain name(s) you are requesting this certificate for.
As mentioned earlier – this guide is assuming you have the ability to add CNAME records for DNS validation that will be coming up after you make the initial request in ACM. Email validation is not going to be covered and is only for those rare use cases you are unable to add CNAME records for the domain.
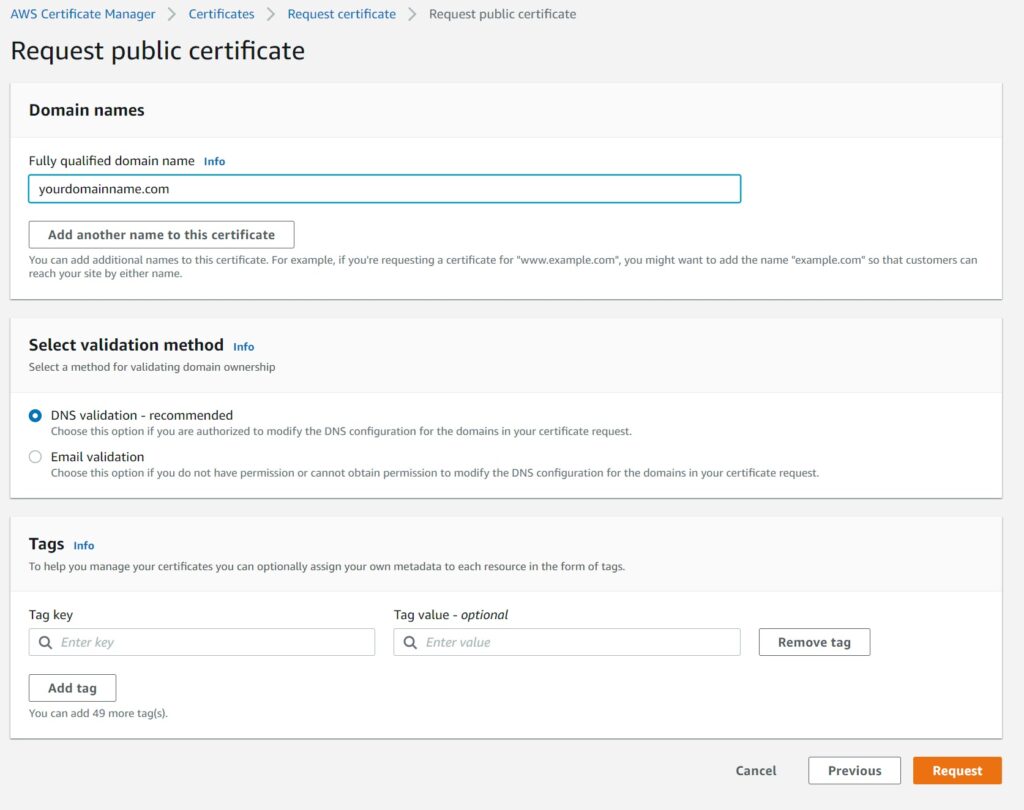
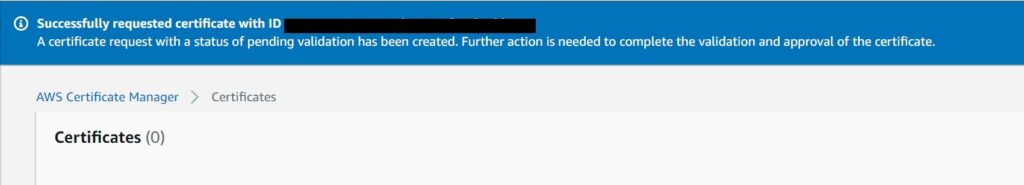
Assuming all went well, you should see this confirmation dialog. The next step is DNS Validation
DNS validation for requested certificate
The certificate is now created by ACM, but will be pending validation before it can be used.
Validation is simply done by adding CNAME records with the keys that ACM created for you in the certificate as shown below.
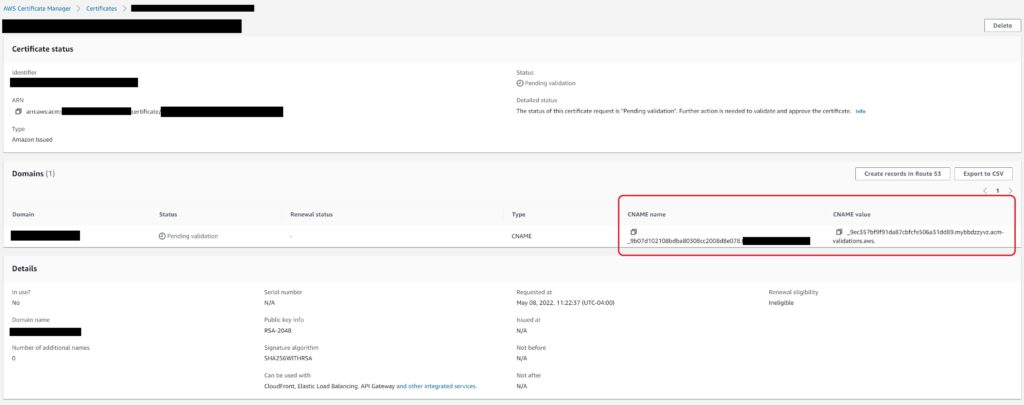
This process is trivially easy if you have the domain on Amazon’s Route 53 – simply click the “Create records in Route 53 Button” to bring up the confirmation window.
And hit create records to get it created.
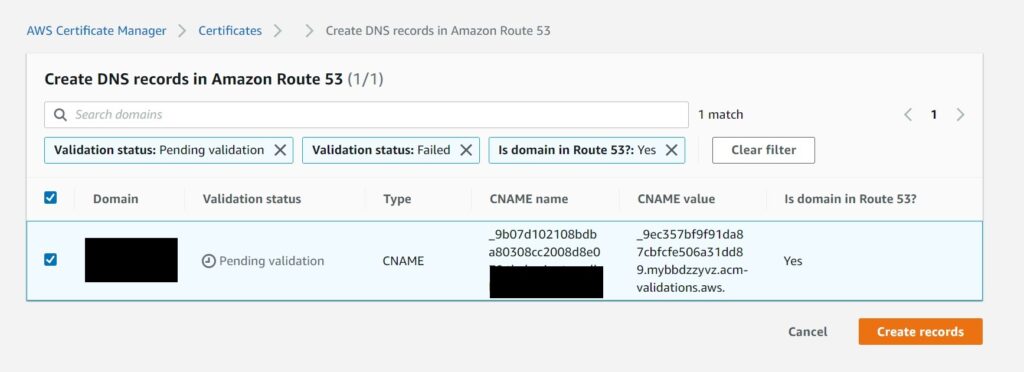
ACM will automatically enter the CNAME records in your Route 53 Hosted Zone for your domain.
You may have to wait up to 30 minutes for the DNS validation to complete, but once it is done, you will be good to go and can confirm it by viewing the status on the certificate details on the ACM console.
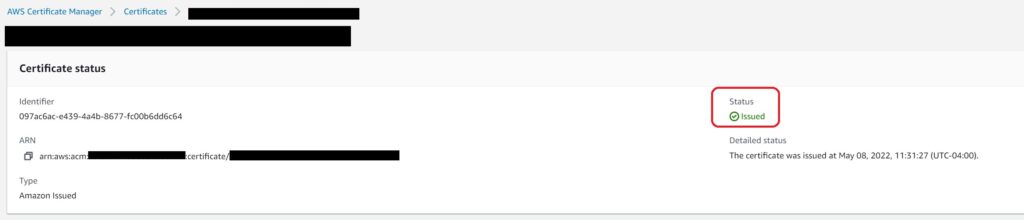
DNS validation if domain is not on Route 53
If you don’t have your domain on Route 53, you will need to add the CNAME details with your own DNS provider database and ACM will keep checking for up to 72 hours after the request was made for the certificate. After this 72 hour period though, ACM will fail the request with a Validation Expired message. At that point you will need to request a new certificate.
Next Steps
If you are using the AWS Certificate Manager issued certificate with other AWS integrated services like API Gateway or Load Balancer – this SSL certificate is free to use. In other cases too, the cost is not significant and you get a lot of the other benefits of working with the ACM console such as the easy management and renewal process for your certificates.
In general I have used both Route 53 and AWS Certificate Manager for both my personal and work related domain and SSL certificate needs and am happy to recommend both these services for your own considerations for use.